Six years after writing the article «We all wanted to be innovative» in July 2017, I revisit some ideas and revisit the topic, as it remains current in everyone’s mind.
In a globalized and constantly changing world, the idea that innovation has become a key element for business success is gaining ground. Companies that are able to innovate constantly are the most likely to stay at the forefront of their industry and outperform their competitors.
But the mere fact of innovating in something (especially when we assimilate it only to creativity), is not a guarantee that the expected success will be achieved. It is necessary to be careful when innovating, to always take into account the strategy that has been proposed, the moment that is lived, the foreseeable trends in the environment and above all that it solves a problem, for which the innovation provides an added value that some traditional solution does not do.
Processes for driving innovation
In order to try to ensure that the products of innovation have a positive impact on our reality, it is necessary to separate it from being a process of almost artistic inspiration, to a process based on a methodology.
Innovation is not a random process. It is important to keep in mind that it is a structured process that facilitates the generation of ideas, their evaluation and implementation.
A typical innovation process can be divided into the following phases:
- Problem identification: Although spontaneous innovation exists, it is not common. Therefore, a very good starting point is a problem to be solved or improved in a different and better way than what already exists.
- Generation of ideas: In this phase, we seek to generate as many ideas as possible to solve the identified problem. Not all ideas will complete the process. In fact, only a small number of them will, so it is important to ensure as many as possible, and to create an environment in which creativity and out-of-the-box thinking will be the main protagonist.
- Evaluation of ideas: The ideas generated must be evaluated to determine their viability and their potential for success. to do so, the environment, the market and trends must be taken into account. This will mark the feasibility of turning the idea into reality. Those that are not very viable are left on the way, but they are not discarded, what is not viable today, may be the perfect solution tomorrow.
- Prototype development: With the ideas that seem viable, prototypes can be made in order to see in a real and practical way the product working. By their nature, prototypes are a fast way to generate a finished product, although still with some limitations, but fully functional. For this it is important that the development team be multidisciplinary, to avoid biases and distortions. Technology should be just one participant among many.
This process can be tailored to the specific needs of each company, but in general, it is a good basis for driving innovation.

Personal qualities for innovation
We all generate ideas constantly, that is part of being human. What holds us back many times is not expressing those ideas, getting frustrated when something doesn’t work and not being able to contribute to someone else’s idea.
That is why there must be a culture of innovation that fosters and drives this creativity, in addition to making people understand that although most of the ideas will fall by the wayside, it does not mean that they are bad ideas. It may be that we do not yet have the right technology or the market is not mature.
Therefore, we must look for people who handle frustration well and see in every failure an opportunity to keep pushing, improving and generating ideas. They must also be able to embrace others’ ideas as their own in order to contribute their own points of view and promote their development in multidisciplinary teams.
It is important to focus on the following qualities:

- Creativity: The ability to generate new and original ideas.
- Problem Solving: The ability to identify and solve problems effectively.
- Adaptability: The ability to adapt to changes and new situations.
- Teamwork: The ability to work collaboratively with people from different disciplines.
Companies can look for these qualities in their recruitment and development processes.
How to handle failure
Innovation involves a certain degree of risk. Some ideas are likely to fail, even after careful evaluation.
It is important for companies to have a positive attitude towards failure. Failure should not be seen as a sign of weakness, but as a learning opportunity.
Companies that have a positive innovation culture encourage experimentation and risk-taking. Employees in these companies feel comfortable sharing their ideas, even if they seem far-fetched.
When an idea fails, it is important to analyze the causes of failure in order to learn from it. This will help the company to improve its innovation processes and reduce the risk of failure in the future.
That is why it is important not to punish failure, this in itself is not bad, because, even if we take all possible precautions, always an idea that may look great at the beginning, can fail completely when we try to apply it to a real environment. We have seen it before.
So, rather than feeling overwhelmed and failed, you have to work on the idea of how you can improve this. What was it that did not go as expected and what changes can be made to reverse that failure. At this point we can even restart the previous process just by changing what, already with the real case, does not work for practical application.
Companies can take the following steps to manage failure:
- Accepting failure: The first stage in handling failure is to accept that it has occurred. Companies should not try to deny failure or blame others.
- Analyze failure: Once the company has accepted failure, it should analyze the causes of failure. This will help the company learn from its mistakes and reduce the risk of failure in the future.
- Learning from failure: The analysis of failure should lead to concrete actions to learn from failure. Companies should implement changes in their processes or culture to reduce the likelihood of failure happening again.
- Continue to innovate: Failure should not discourage companies from continuing to innovate. Companies should learn from failure and continue to look for new ideas to improve their products and services.
Conclusions
Innovation is a key part of business success. Companies that are able to effectively drive innovation are more likely to achieve their goals and stay at the forefront of their industry.
Companies can drive innovation by implementing a structured process, finding people with the individual qualities needed for innovation and adopting a positive innovation culture.






 A farmer had 30 sheep that he had to take out to pasture every day at the beginning of the day, to return them to his barn at night.
A farmer had 30 sheep that he had to take out to pasture every day at the beginning of the day, to return them to his barn at night.
 We believe that by filling ourselves with successful and skillful strikers in all positions of a soccer team, we are guaranteed to win every game and we are not.
We believe that by filling ourselves with successful and skillful strikers in all positions of a soccer team, we are guaranteed to win every game and we are not.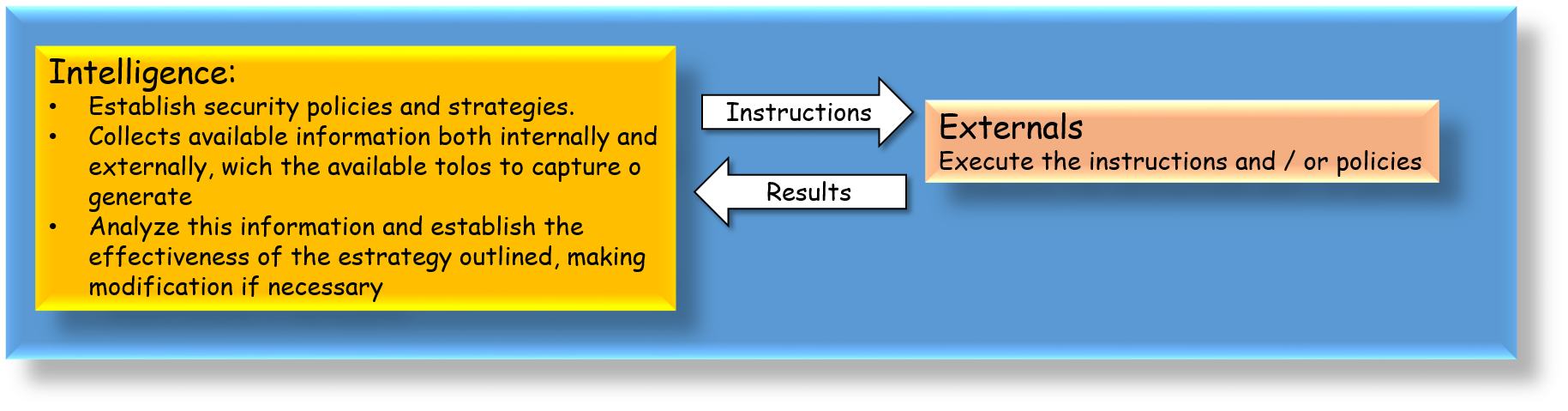



 Establishing a common thread that mark the CIO’s work, whatever the company or industry in which he operates is not easy. Each company, even if they belong to the same industry, has its own particularities, typical of an organization that, when formed by people, is changing permanently in its organizational culture and in its processes, especially in the present day in which the environment demands a quick and constant adaptation to it.
Establishing a common thread that mark the CIO’s work, whatever the company or industry in which he operates is not easy. Each company, even if they belong to the same industry, has its own particularities, typical of an organization that, when formed by people, is changing permanently in its organizational culture and in its processes, especially in the present day in which the environment demands a quick and constant adaptation to it.
 I definitely believe that the break-in of WannaCry changed the scenario in which technology has been moving until now.
I definitely believe that the break-in of WannaCry changed the scenario in which technology has been moving until now.





 I have read some articles and opinions these days about whether the various IT C-Levels that have emerged in the last time, must be hierarchically dependent on each other, or all should be reporting directly to the CEO, or some mixed scheme.
I have read some articles and opinions these days about whether the various IT C-Levels that have emerged in the last time, must be hierarchically dependent on each other, or all should be reporting directly to the CEO, or some mixed scheme.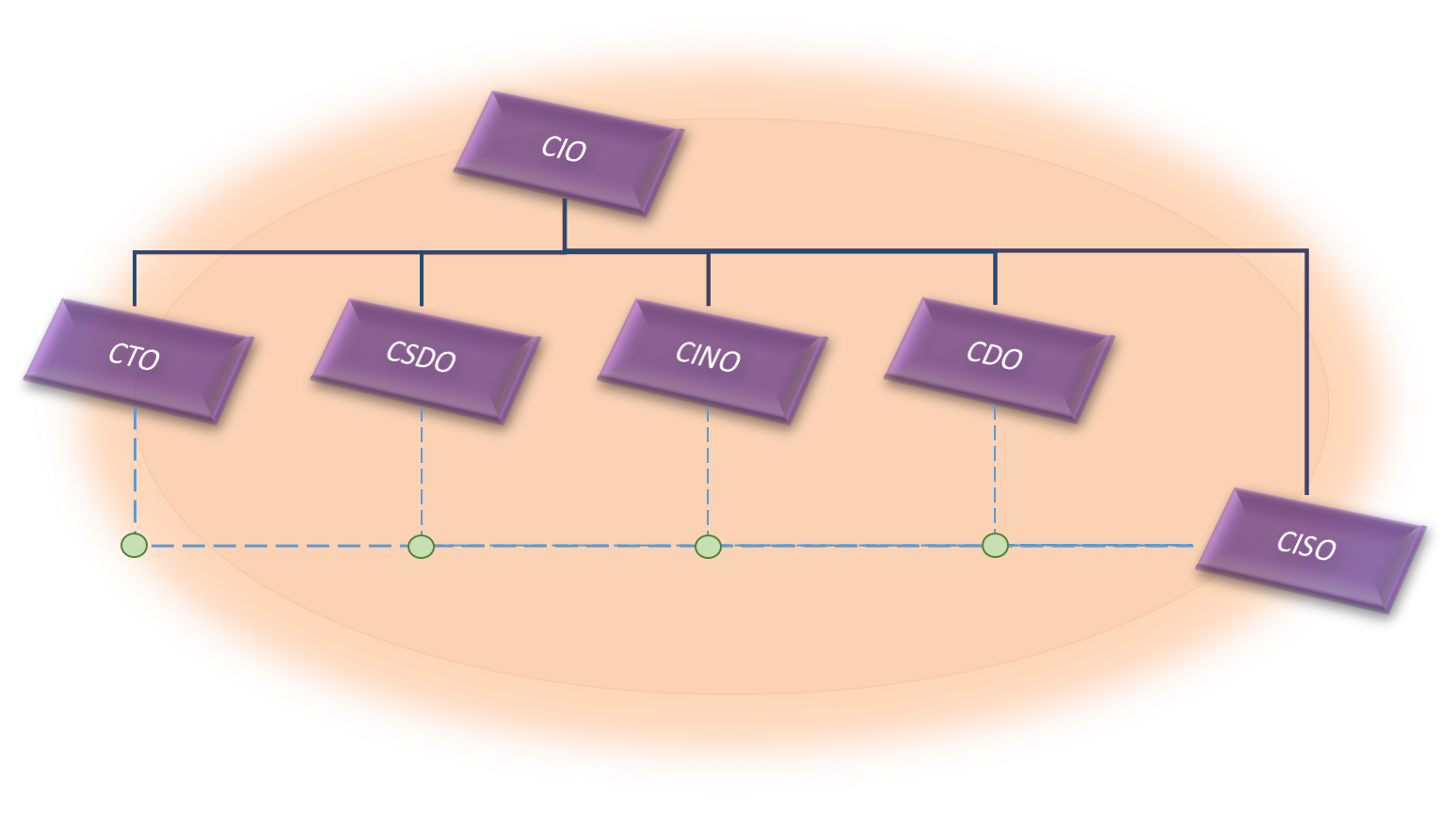
Comentarios recientes